Photo: libre-software.net. License: CC BY-SA 4.0
How to set up automatic updates on Ubuntu Server 20.04, 22.04 or 24.04
Last updated on May 27, 2024
This guide explains how to configure automatic updates in Ubuntu Server 20.04 “Focal Fossa”, Ubuntu Server 22.04 “Jammy Jellyfish” or Ubuntu Server 24.04 “Noble Numbat”.
Step 1: package installation
Install the unattended-upgrades package:sudo apt install unattended-upgrades
This package may already be installed on your server.
Step 2: configure automatic updates
Edit the configuration file (here with nano – replace with any other text editor):sudo nano /etc/apt/apt.conf.d/50unattended-upgrades
The beginning of the configuration file should look like this:
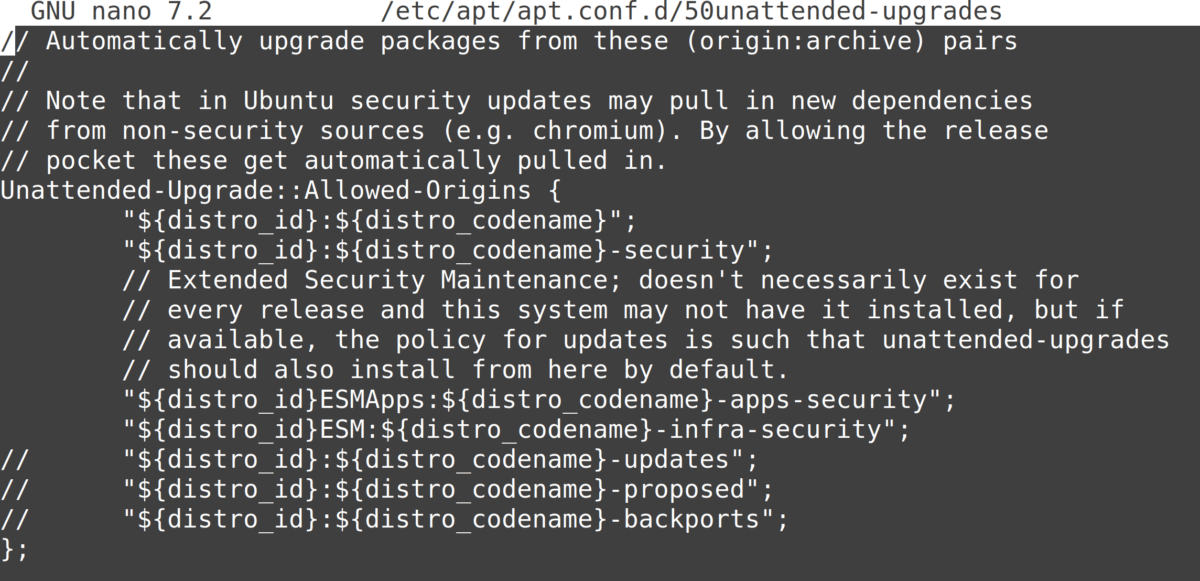
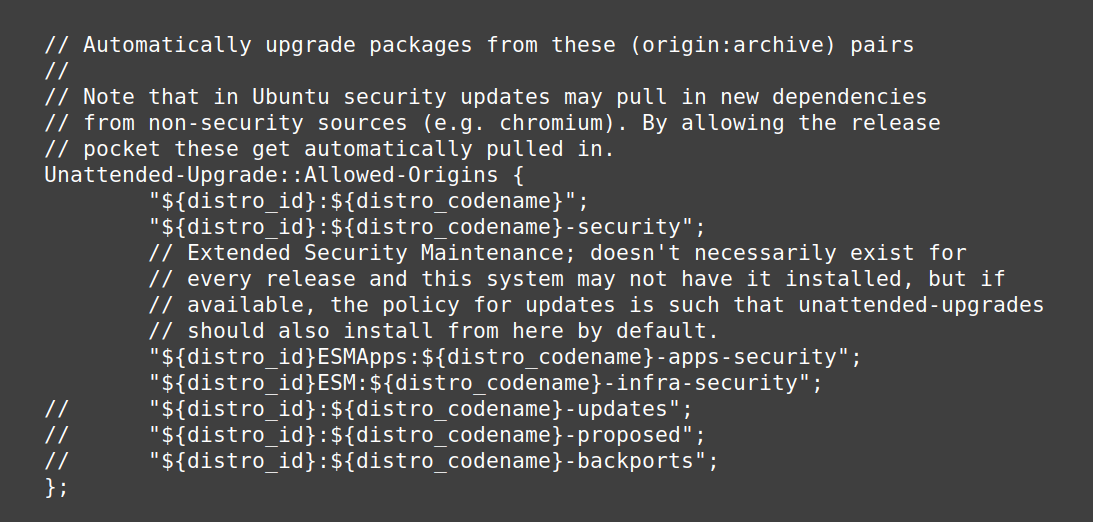
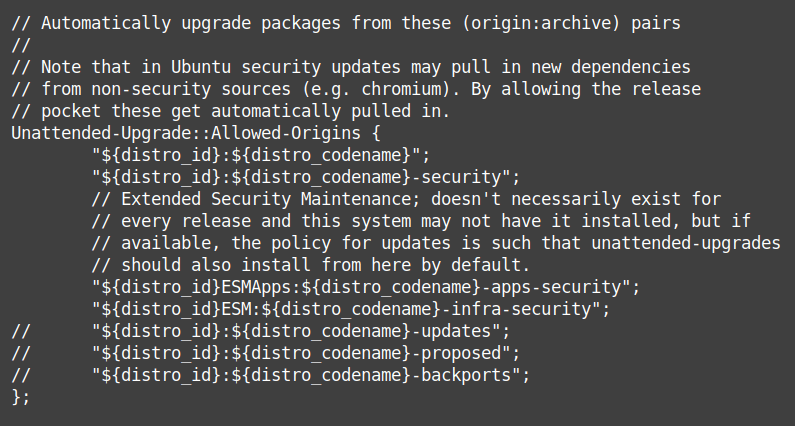
Anything after a double slash “//” is a comment and has no effect. To “enable” a line, remove the double slash at the beginning of the line (replace with nothing or with spaces to keep alignment).
The most important: uncomment the “updates” line by deleting the two slashes at the beginning of it:"${distro_id}:${distro_codename}-updates";
Recommended: remove unused kernel packages and dependencies and make sure the system automatically reboots if needed by uncommenting and adapting the following lines:Unattended-Upgrade::Remove-Unused-Kernel-Packages "true"Unattended-Upgrade::Remove-New-Unused-Dependencies "true";Unattended-Upgrade::Remove-Unused-Dependencies "true";
Unattended-Upgrade::Automatic-Reboot "true";
Unattended-Upgrade::Automatic-Reboot-Time "02:38";
To save your changes in nano, use Ctrl + O followed by Enter. To quit, use Ctrl + X.
How to get email notification after automatic updates
Uncomment and adapt the following lines to ensure you’ll be notified if an error happens:
Unattended-Upgrade::Mail "user@example.com";Unattended-Upgrade::MailReport "only-on-error";
Please note: your server needs to be able to send emails – which is mostly not the case by default! If you didn’t install and configure Postfix on your server, email notifications will NOT work.
Step 3: enable automatic updates
Enable automatic updates and set up update intervals by running:sudo nano /etc/apt/apt.conf.d/20auto-upgrades
In Ubuntu 22.04 and 24.04, the file has only the following two lines by default:
APT::Periodic::Update-Package-Lists "1";APT::Periodic::Unattended-Upgrade "1";
Insert the following lines at the end of the file:
APT::Periodic::Download-Upgradeable-Packages "1";APT::Periodic::AutocleanInterval "7";
The time interval is specified in days, feel free to change the values. In total, you should have all four lines. Save changes and exit.
Step 4: check if it works
You can see if the auto-upgrades work by launching a dry run:sudo unattended-upgrades --dry-run --debug
The dry-run may output something like this:
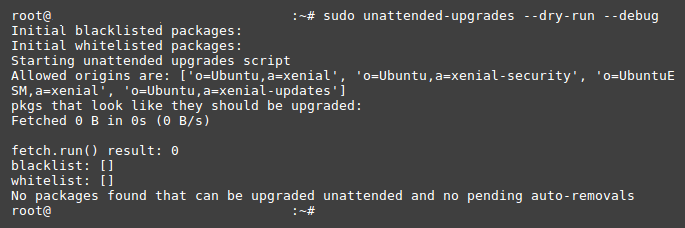
Depending on your server configuration, the output may look less clean, which is OK:
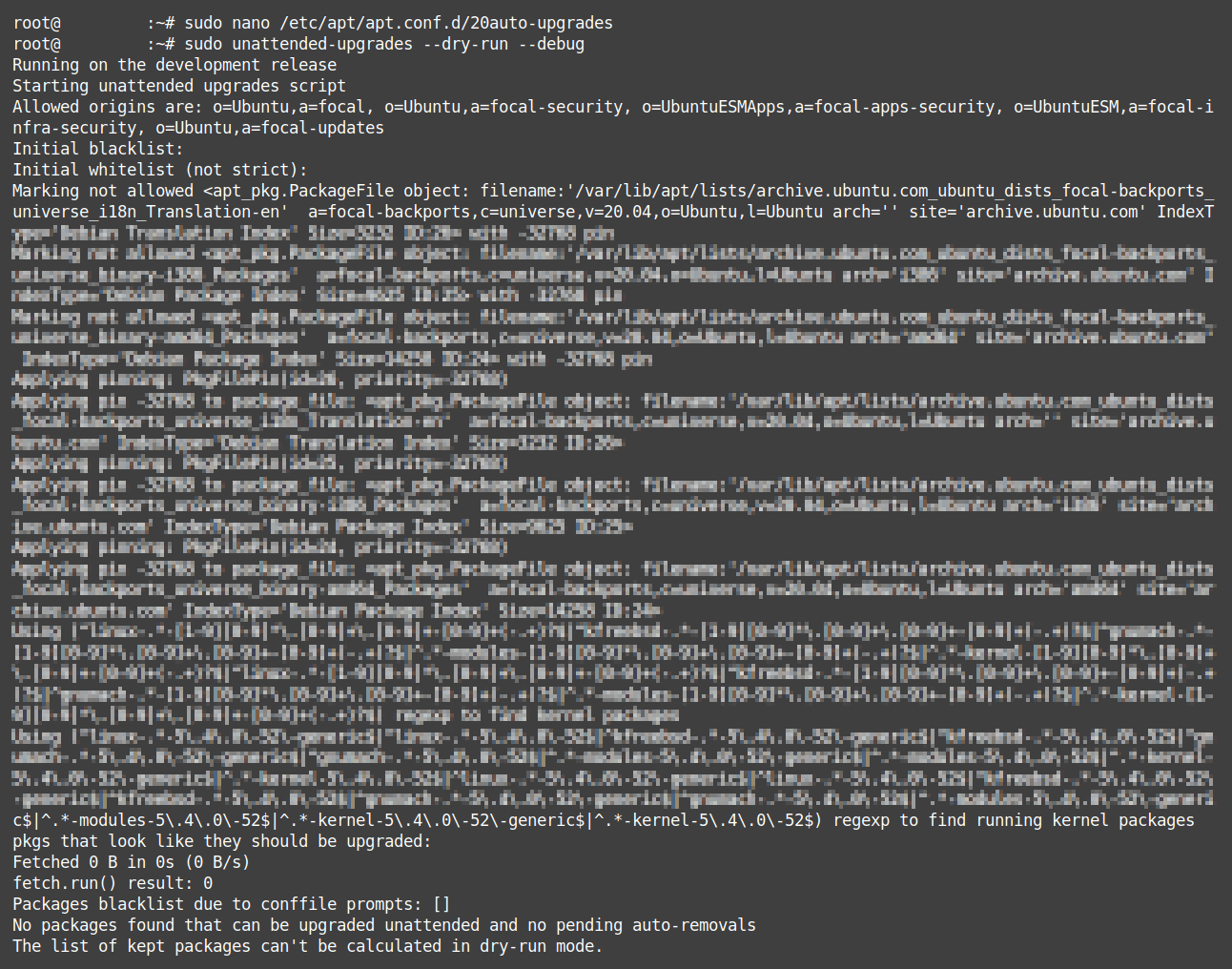
Another way to check if automatic updates work is waiting a few days and checking the unattended upgrades logs:cat /var/log/unattended-upgrades/unattended-upgrades.log
Done! Ubuntu Server 20.04 / 22.04 / 24.04 should now update itself once a day.
By Johannes Eva, April 2018 – May 2024







29 thoughts on “How to Install Firefox on Linux Mint, Ubuntu, Debian or any other Linux distribution”
Thank you John! Yes, Thunderbird can be installed/upgraded the same way 🙂
I was wanting to update Firefox on my Ubuntu Trusty (14.04). I finally came across this article and … tahdah. Now I have Firefox 83 installed and working perfectly. Thank you so much for this article. One question – can I also install the latest Thunderbird in the same manner?
And please folks, no comments like – just upgrade to the newest Ubuntu. Trusty works perfect. I have Apache installed and it works perfect also. So why should I update/upgrade to a newer version when I have perfection now. You know the old saying – If it works don’t fix it.
You may have to create the
/optdirectory first:sudo mkdir /optGood luck!
Hello, I’m French.
It’s hard to me to understand English so when it’s electronic language, it’s very very hard. But I tried (even if I doesn’t understand, even while translating). And when I tried, I succeed to extract the file (yeeaah!) but I can’t move Firefox to
/opt, it says “no such file or directory” like Kurman (an other user). But how am I doing now ? I search a lot of solutions and nothing works. Netflix doesn’t want to work with my old Firefox (the 66.0.3 version). Am I going to get there someday? After Netflix, it will be some important things…Please, help me. (Once I could watch Netflix…)
Thanks for the article!
Note: When the default version of Firefox is upgraded by the system, the symlink
/usr/bin/firefoxis overwritten and you will either have re-create it or just lock the currently installed version in Synaptic to prevent that from happening altogether:Thank you for your comment and for the correction!
Great article. In the case of Firefox newer is better. Every update since Quantum debuted has brought it closer to perfection. Oh, I think it may be ‘inexperienced’, rather than ‘unexperienced’. Regardless, the advice is sound.
It’s always best for newbies to practice caution. Then again, it took a few self inflicted system meltdowns to really start getting the hang of this Linux thing.
@Rafael: no, you won’t loose your Firefox settings. These are stored in your profile folder. On Linux, you profile folder is in your home directory, in the
.mozilla/firefoxsub-folder. You may need to show hidden files and folders (use Ctrl + H or the “View” menu) to navigate to the profile folder.If you only have one profile, its folder has “default” in the name. The complete path of the Firefox profile folder will be something like:
/home/user_name/.mozilla/firefox/random_string.defaultThis folder allows for an awful lot of flexibility, for example you can:
If I just remove the old Firefox folder in
/opt, what about my favorites settings? Am I gonna lost it all?Thank you, this is indeed useful. Installing Firefox from .deb packages is also a viable option. Keep in mind that the recommendation is the same as when installing from the tar.gz archive: “it is strongly suggested to use a package manager like aptitude or synaptic to download and install packages, instead of doing so manually via this website.”
Is easier get it there: https://packages.debian.org/sid/amd64/firefox/download
Make friends with the terminal!
Sure, it’s been quite some time since 2015: Users must extract from the “tar” archive and use a password-enabled (root) terminal (or sudo) to perform the subsequent file actions. Simply invoking a file manager and then copying/pasting won’t work.
The reason Debian users end up here:
Note that Debian’s repository version of Firefox still is named “firefox-esr,” not simply “firefox” (Before, it was “iceweasel” – a legality, still in effect with firefox-esr): Debian proves perhaps the most conservative distro in the Linux realm. As was noted in an old saying: “They wear both a belt and suspenders!”
The problem is that institutions performing secure transactions (say, global financial corporations) – along with many still-perplexed users (who generally aren’t bare novices) – dislike legacy browser versions. Debian purists dislike the corporate bent of Mozilla’s Firefox development. (After all, it’s firefox.com, not firefox.org.)
Thank you. Simple, clear and helpful. Works for me on Linux Mint (64 Bit)
Kumar, you’re probably in the wrong directory when running the
movecommand – or using the wrong file name. Using the TAB key to autocomplete the file name helps to know if you’re right: if it autocompletes the file or directory names, it’s right, else it’s wrong. Of course, listing files with thelscommand also shows if you have extracted the archive correctly.I’ve extracted the file but I can’t move it to
/opt, it says no such file or directory.For future reference,
tar xf filewill deal with the compression without having to specify it.I also run Mint 17.3, the Firefox version is 45 and it should be updated to 46 very soon. I can’t explain why you’re stuck with an older version. I suppose you ran
sudo apt-get update? If nothing else works, I would suggest to install the newest Firefox version manually as described in this guide.Update: The update to Firefox 46 just showed up in the update manager. It took 4 days to the Linux Mint team to check and distribute the update, which is fine.
You state here, and I’ve seen in other places, that Debian-based package managers will release firefox updates “just a few days after the official release”. That has not been my experience. I run Linux Mint 17.3, and as of today (4/30/2016), my firefox from the package manager is version 42.0. The following version (43.0) was released 4.5 months ago on December 15th, and version 46.0 was released this week. What am I missing?
Pingback: Install the latest FireFox in CentOS 7 - UncleNinja
Pingback: Upgrade Firefox di Linux Mint | Catatan dan Wiki Personal
The Tab Groups (Panorama) feature has been discontinued. There are Firefox add-ons with similar features, check the official announcement from Mozilla:
https://support.mozilla.org/en-US/kb/tab-groups-removal
FF 45 in Mint does not open groups of tabs anymore. So that seems broken.
I went back to a former version. The repository only offered FF 28… But this one still works.
I figured out something, I turned off check for default application in settings (during start of application, it ignored it 🙂 ) I hope it will work
I have other problem 🙂 I unpacked firefox (did same with thunderbird), created symbolic links and everything, but still, when I run firefox or thunderbird, it said it is not default browser/email client and I can’t turn it off. It is not really functional problem, but it is reaaaaaally annoying 🙂 in preffered applications is set firefox and thunderbird (the original mint firefox and thunderbird don’t have this problem), is there any way (and I am sure there is) how to set unzipped TB and FF as default? BTW I am using common profiles for windows and for mint 17.3 in both applications. THX 🙂
Well, in fact this tutorial is for advanced users, most of which are installing Firefox on their own on custom Linux systems. Or trying Firefox Beta/Aurora or other special versions of Firefox.
In your case you’re probably using mainstream distributions such are Ubuntu, Linux Mint, Debian, OpenSuse, Fedora, … The package manager of your distro will take care of updating Firefox by itself, when when the new Ffox version has been tested for compatibility with your distro, so that it doesn’t break anything. On Ubuntu or Linux Mint, for example, it takes just a few days after the official release.
Please do NOT use this guide to update Firefox by hand if you’re just a “normal” user or a Linux beginner. Just apply the normal updates (as you should always do) for your distribution and you’ll get the new Firefox version. I’ll try to make a version of this guide for beginners and normal users soon, as it seems to be really confusing. Sorry for that.
I really do try to like Linux… but I just can’t understand why I can’t just UPDATE my firefox in one click? The version is there – why do I need to start entering commands and copying folders for something as trivial as that?
Pingback: How to install Firefox 43 on Linux Mint, Ubuntu, Debian, CentOS, Fedora - Free Networking Tutorials, Free System Administration Tutorials and Free Security Tutorials
Ubuntu will take care of Firefox upgrades automatically, you don’t have to do it manually. It may take a few days after the official release for the Firefox upgrade to show on, because the Ubuntu folks have to test the new release with Ubuntu.
There is no Firefox install in
/optby default, as this is where admins/users are supposed to install optional software. If you did not install anything in/optmanually, nothing show up there, which is normal.Hope this helps!
How do I upgrade the current installation with the tar.b2? I’m on Ubuntu-Mate-15.10 & it doesn’t appear to be in the /opt directory.
Comments are closed.